Your corporate network should be an impenetrable fortress, safeguarding your most valuable assets. But a virtual private network (VPN) is like a massive front door that’s always open—visible and accessible to attackers around the world. This isn’t just a security risk; it’s a glaring vulnerability that threatens your entire infrastructure.
The VPN Vulnerability Trap
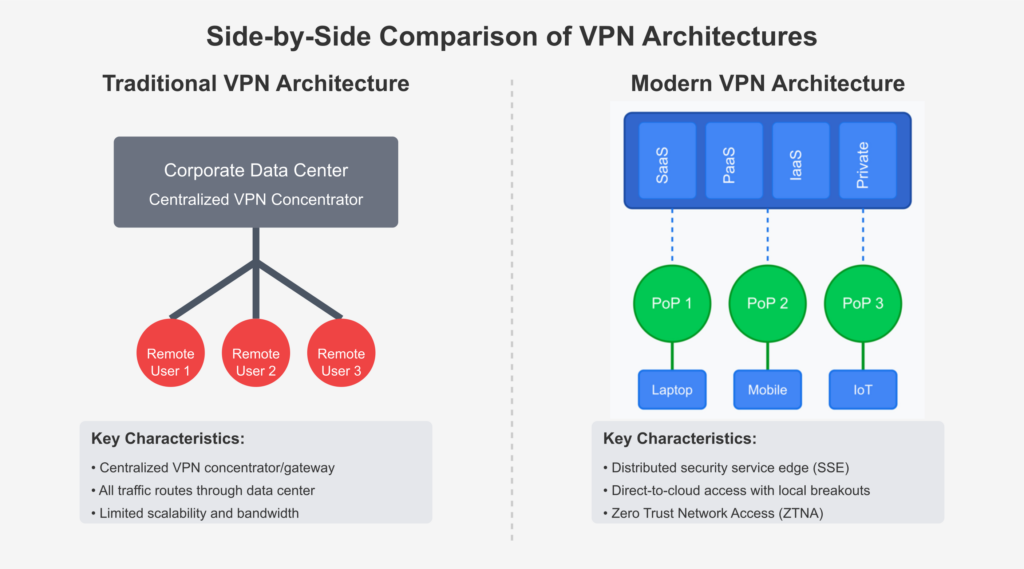
Traditional VPN Architecture (Left Side)
- Relies on a centralized VPN concentrator, routing all remote user traffic through a corporate data center.
- This single-point-of-entry creates security risks and bottlenecks, limiting scalability and bandwidth.
- Users connect from various locations (home, mobile, remote offices), but all data must first pass through the central hub, increasing latency and congestion.
Modern VPN Architecture (Right Side)
- Uses a distributed security service edge (SSE) model, reducing dependency on a single access point.
- Traffic is routed directly to cloud services (SaaS, PaaS, IaaS, private resources) through multiple Points of Presence (PoPs), improving performance and reducing latency.
- Implements Zero Trust Network Access (ZTNA), ensuring users only access specific resources based on identity, device, and security posture.
Traditional VPNs were groundbreaking when first introduced, enabling remote work by connecting employees to corporate networks from anywhere. However, these same technologies have now become a critical security liability.
The fundamental problem is brutally simple: VPNs require maintaining a public-facing gateway into your private network. It’s like leaving a front door wide open, with a welcome mat that says “try to break in” to every cybercriminal on the planet.
The Attacker’s Perfect Entry Point
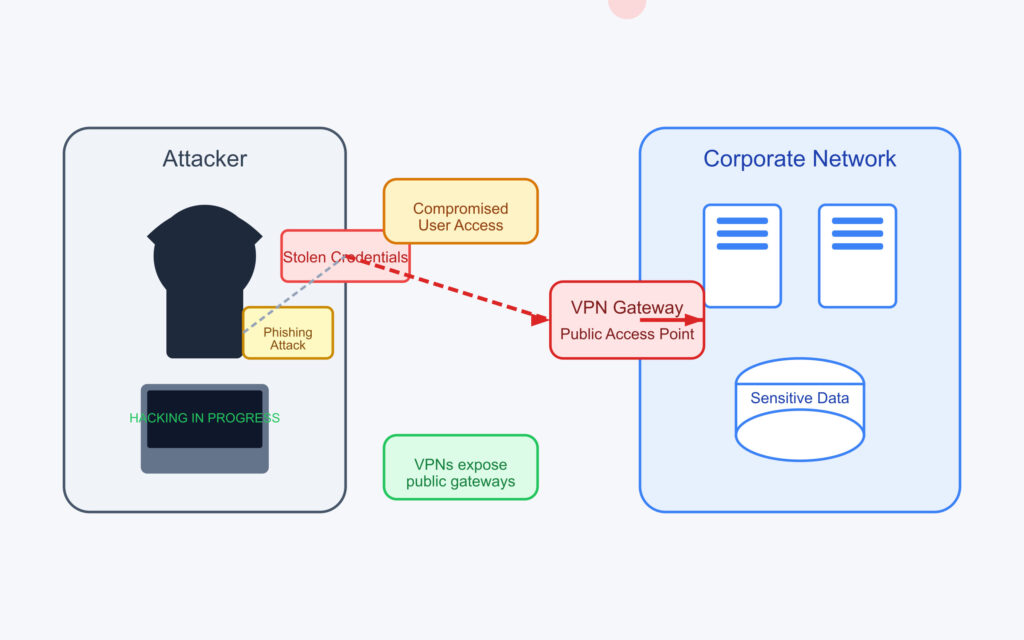
Here’s how a typical attack unfolds:
• Attackers obtain valid credentials through phishing, social engineering, or brute force.
• They now have a legitimate, encrypted tunnel directly into your internal network.
• Once inside, they can move laterally with remarkable ease.
Traditional VPN architectures typically grant broad network access, meaning a single compromised credential becomes a skeleton key to your entire infrastructure. One successful credential theft transforms your “secure” connection into an attacker’s ultimate playground.
The Zero Trust Revolution
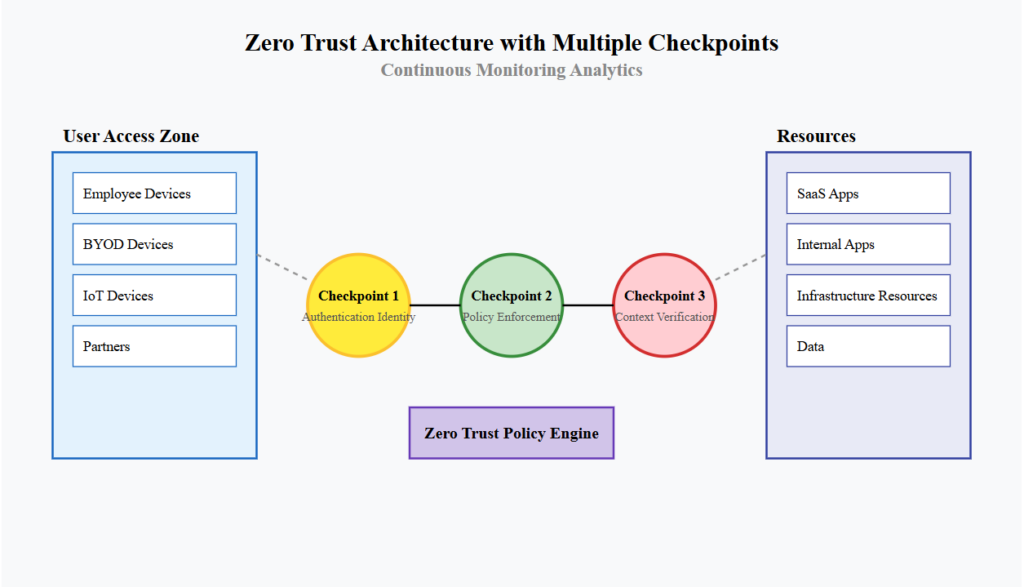
Modern cybersecurity demands a fundamentally different approach. Zero Trust architectures eliminate the vulnerable gateway model entirely by:
• Removing public entry points
• Implementing identity-based access controls
• Utilizing micro segmentation
• Enforcing least-privilege principles
• Securing individual resources, not entire networks
Instead of a single, vulnerable front door, Zero Trust creates multiple, tightly controlled checkpoints. Each access attempt is verified, authenticated, and granted only the minimal necessary permissions.
The Stakes Are Real

Every day you maintain a traditional VPN is another day you’re gambling with your organization’s security. Attackers are continuously developing more sophisticated methods to exploit these legacy technologies.
Make The Zero Trust Leap
The choice is clear: continue using outdated, vulnerable VPN technologies or embrace a modern, robust security model that was designed for today’s complex threat landscape.
Zero Trust is the way forward—it’s a security philosophy that assumes no user, device, or network connection should be automatically trusted. It’s time to make that philosophy your reality.
The attackers are waiting. Are you ready to shut the door?
NOVA’s Recommendation: Twingate – A Promising Solution for Secure Access

As organizations move beyond outdated VPN technologies, Twingate stands out as a powerful Zero Trust solution designed for the modern security landscape. Unlike traditional VPNs that rely on a vulnerable gateway model, Twingate’s cloud-native architecture ensures secure, scalable, and seamless access control.
At NOVA Cloud, we’ve rigorously tested Twingate’s capabilities and can confidently recommend it as a superior alternative to legacy VPNs. As a trusted Twingate MSP partner, we help our clients implement this cutting-edge solution, delivering:
✅ Seamless integrations with existing applications and workflows
✅ Granular, identity-based access controls, enforcing least-privilege principles
✅ Full visibility and control over user and device interactions
✅ Adaptive security that evolves with emerging threats
By partnering with Twingate, NOVA Cloud is enabling organizations to embrace a true Zero Trust security model—one that closes the door on cyber threats and strengthens defenses against even the most sophisticated attacks.
The time to act is now. VPN vulnerabilities are a thing of the past. Let’s fortify your digital infrastructure together. Contact NOVA Cloud today to see how Twingate can revolutionize your security strategy.
